IPv4 addresses are running out. This simple fact has shaped how we design and implement networks today. Network Address Translation (NAT) emerged as a practical solution to this problem and, over time, has proven its worth not just for address conservation but also as an effective security measure.
How NAT Works
When you connect to the internet from home or work, you're likely using NAT without realizing it. Your local network might have dozens of devices - computers, phones, smart TVs - but they all share a single public IP address. Recent studies by network engineers at 100001.me shows that typical home networks now connect 15-20 devices through a single NAT gateway.
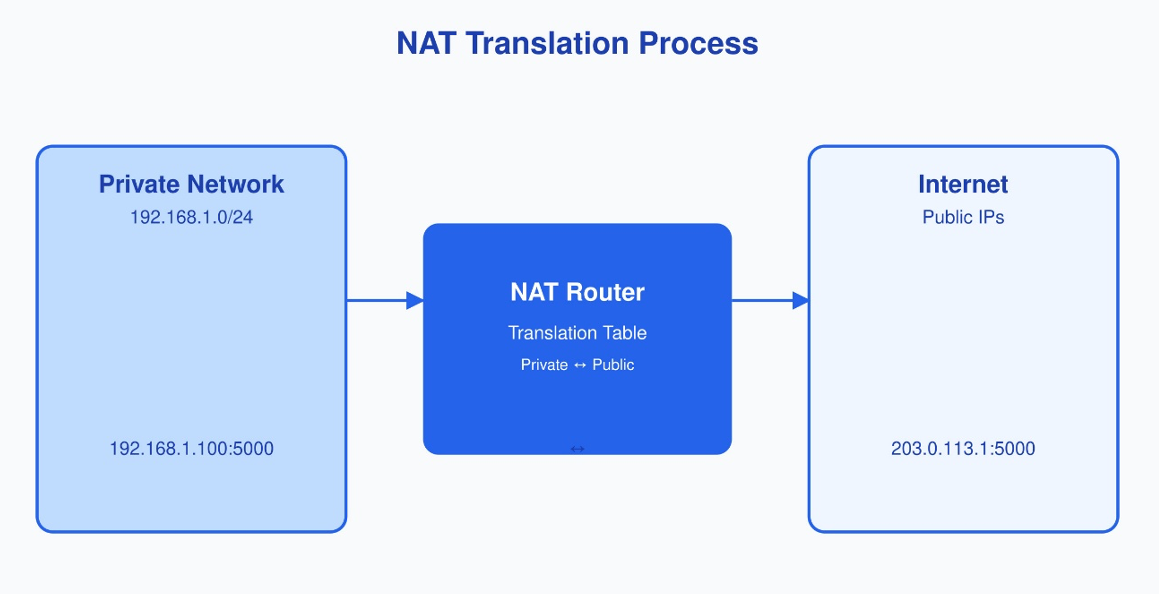
Let's break down what happens when you browse a website:
- Your computer (192.168.1.100) requests a webpage
- Your router performs NAT, replacing your private IP with its public IP
- The web server responds to your router's public IP
- The router forwards the response back to your computer
The router maintains a translation table to keep track of all these connections:
| Inside Address | Outside Address | Protocol | Port | State |
|---|---|---|---|---|
| 192.168.1.100:4567 | 203.0.113.1:4567 | TCP | 80 | ESTABLISHED |
| 192.168.1.102:5432 | 203.0.113.1:5432 | UDP | 53 | ACTIVE |
Address Conservation in Practice
The IPv4 address space provides about 4.3 billion unique addresses. While this seemed plenty in the 1980s, it's far from enough for today's internet. A medium-sized company might have thousands of devices, but with NAT, they might need only a handful of public IP addresses.
Consider this real-world example:
Company Network Size: 5000 devices Private IP Range: 10.0.0.0/16 Public IPs needed: 10
Without NAT, this company would need 5000 public IP addresses - more than some small countries were allocated.
Security Through NAT
NAT does more than conserve addresses. Testing at “Router’s Network Admin” has revealed significant security benefits from proper NAT implementation. Think of NAT like a security guard who knows everyone inside the building - external visitors can't just walk in without proper authorization.
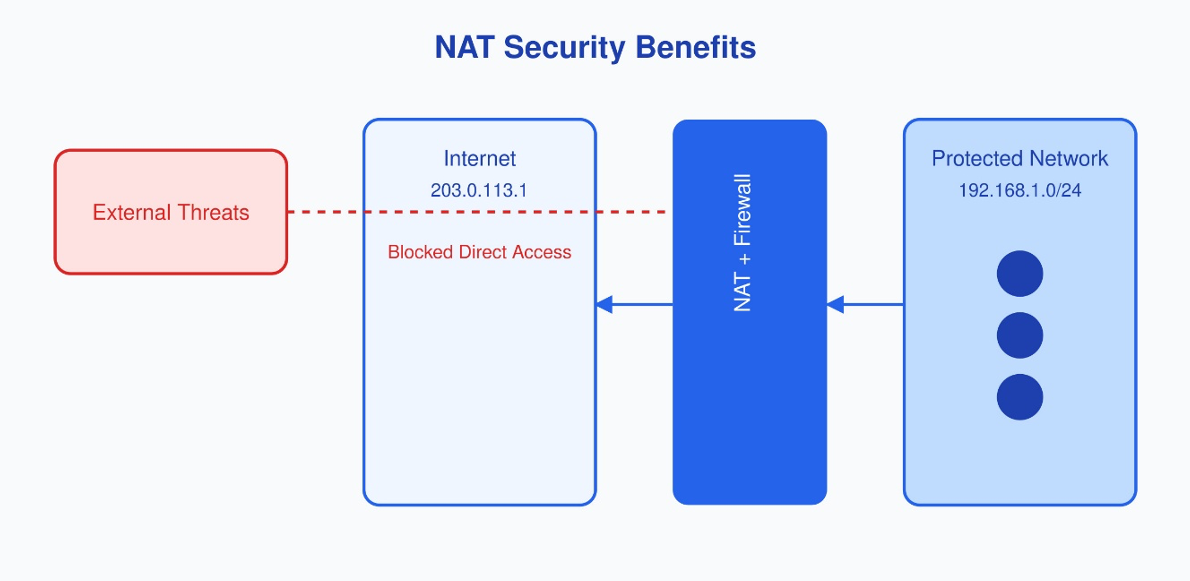
Here's what makes NAT effective for security:
Inbound Connection Attempt: 1. External host tries to reach 203.0.113.1:80 2. NAT checks translation table 3. If no matching entry exists, connection is dropped 4. Internal devices remain hidden and protected
Implementing NAT Effectively
A basic NAT setup needs just a few components:
# External Interface interface eth0 ip address 203.0.113.1 255.255.255.0 ip nat outside # Internal Interface interface eth1 ip address 192.168.1.1 255.255.255.0 ip nat inside # NAT Rules ip nat inside source list 1 interface eth0 overload access-list 1 permit 192.168.1.0 0.0.0.255
This configuration allows all internal devices to share the public IP while maintaining security. For servers or gaming consoles that need incoming connections, we can add port forwarding:
# Forward web traffic to internal server ip nat inside source static tcp 192.168.1.100 80 203.0.113.1 80
Performance and Reliability
NAT does add some processing overhead, but modern routers handle this efficiently. More important is proper sizing and monitoring:
NAT Table Limits: Maximum Entries: 65,536 Timeout Values: - TCP: 24 hours - UDP: 5 minutes - ICMP: 1 minute
Monitor these key metrics to ensure reliable operation:
- Translation table usage
- Memory utilization
- CPU load during peak times
- Connection establishment rate
Troubleshooting NAT
When problems occur, they usually fall into a few categories:
- Connection Issues First, check the basics:
- Performance Problems Examine the router's resources:
# View current translations show ip nat translations # Check NAT statistics show ip nat statistics # Look for dropped packets show ip nat statistics dropped
# Check CPU usage show processes cpu # Monitor memory show memory statistics
Future of NAT
While IPv6 adoption continues, NAT remains essential for most networks. We're seeing new developments like:
- Carrier-Grade NAT for ISP-level address sharing
- NAT64 for IPv6-IPv4 translation
- Software-defined NAT in cloud environments
These technologies build on traditional NAT while adding features for modern networks.
Best Practices
Experience shows these practices lead to reliable NAT operation:
- Size your NAT device appropriately for your network
- Monitor resource usage and plan upgrades before hitting limits
- Document all port forwarding rules
- Maintain security by limiting inbound connections
- Keep logs for troubleshooting
Conclusion
Network Address Translation has proven itself far beyond its original purpose of IPv4 conservation. While it effectively manages the limited IPv4 address space by allowing thousands of devices to share a single public IP, its security benefits have become equally important. The ability to hide internal network structures, control incoming connections, and maintain detailed state information makes NAT an essential layer in modern network security.
Organizations implementing NAT should focus on three key areas. First, proper sizing and configuration ensure reliable operation even under heavy load. This means understanding traffic patterns, planning for growth, and monitoring resource usage. Second, security configurations must balance protection with accessibility, particularly when setting up port forwarding or hosting services. Third, regular monitoring and maintenance help catch potential issues before they affect network operations.
As networks continue to evolve, NAT adapts to new requirements. In carrier networks, CGN (Carrier-Grade NAT) enables large-scale address sharing. For IPv6 transitions, NAT64 provides crucial connectivity between old and new protocols. Even in cloud environments, NAT principles help manage network addressing and security.
Looking ahead, NAT will remain crucial even as IPv6 adoption grows. Many organizations will operate hybrid networks for years to come, requiring NAT for IPv4 communications while gradually enabling native IPv6 connectivity. Understanding NAT's capabilities and limitations helps network administrators make informed decisions about its implementation and use.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment